How to set up and use Pretty Good Privacy (PGP) for secure communication

Pretty Good Privacy (PGP) is one of the most effective email and file encryption protocols, but its complexity makes it inaccessible for most people. If you’ve ever tried to use PGP before, you can probably attest to how complicated it can be to generate, share, and manage your PGP encryption keys.
Fortunately, modern PGP services automate many of the cumbersome processes. In turn, this makes it easier for anyone to set up and benefit from email encryption.
This article will give you a quick introduction on what PGP is, how it works, what it’s for, and how you can start using it.
What is Pretty Good Privacy (PGP)?
PGP is a method of protecting digital communication and files using public-key cryptography, where each user has a pair of linked keys: a public key that can be shared and a private key that is kept secret.
When someone sends you an encrypted message with PGP, the content is first encrypted with a temporary symmetric key. That symmetric key is then encrypted using your public key. Only your private key can decrypt the symmetric key, which in turn decrypts the message.
PGP also lets you digitally sign messages and files. When you sign something with your private key, anyone with your public key can verify that it truly came from you and hasn’t been altered. This protects both the privacy and integrity of your secure communications.
Today, PGP is represented through the OpenPGP standard, which is a modern, publicly available, open-source-friendly, and interoperable version of the original PGP system. OpenPGP ensures that any software following its rules can securely exchange encrypted and signed data with any other OpenPGP tool, meaning you’re not locked into one company’s product(s).
It’s also worth saying that PGP and OpenPGP are essentially interchangeable terms at this point. If someone talks about using PGP encryption, they’re typically talking about a tool or software that uses OpenPGP.
PGP also shouldn’t be confused with other encryption software, like a VPN. It exists in a broad range of other cybersecurity tools and serves to encrypt messages, files, and similar content.
PGP uses
Although PGP is commonly used for encrypting emails, it also has various other applications. Here are a few examples of content that benefits from PGP encryption.
Email encryption
As mentioned, this is the main use case for PGP. Encrypting emails with PGP means only the person holding your intended recipient’s private key can read your message. This stops third parties, including email providers, local government bodies, or cybercriminals, from spying on your conversations.
Once you’ve exchanged public keys, most modern tools handle encryption and decryption automatically. You keep the same inbox, but the contents of each email are locked up. Essentially, PGP turns a regular email service into a secure channel without needing an entirely separate messaging platform.
Digital signature verification
PGP isn’t just about keeping data secret; it also proves the legitimacy of the sender. When you sign a message or file with your private key, it creates a unique cryptographic signature tied to both you and that content.
Anyone with your public key can verify the signature to confirm that the message genuinely came from you. This stops anyone from slipping in forged emails or tampered documents. This aspect of PGP is especially important for businesses.
This aspect is also commonly used on the dark web. For example, online marketplaces will regularly post their PGP keys in public key servers so customers can find them and verify their legitimacy.
File encryption
You can also use PGP to encrypt any of your local files. You essentially have two options for using PGP with files. Encrypting a file with someone’s public key means only their private key can decrypt and open it. You can also encrypt files for yourself. Either way, this offers protection against any threat actors who gain unauthorized access to your computer.
How does PGP encryption work?
PGP encryption works by combining symmetric and asymmetric cryptography to ensure secure message transmission. Here’s a step-by-step breakdown of the process: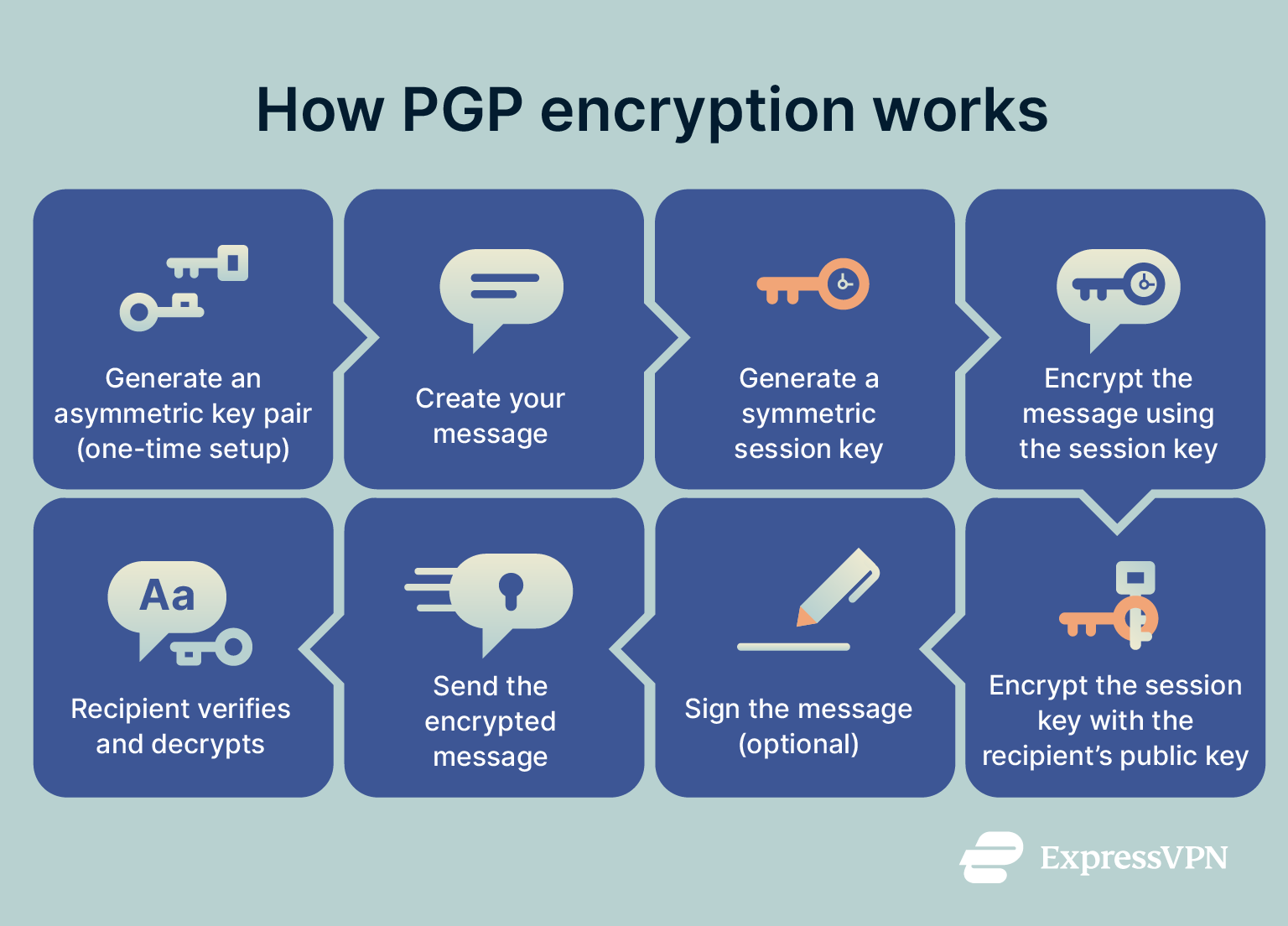
- Generate an asymmetric key pair (one-time setup): Before sending or receiving encrypted messages, each user must generate a public-private key pair using PGP software. The public key is shared with others so they can encrypt messages to you. The private key is kept secret and used to decrypt incoming messages and to sign messages for authenticity.
- Create a message: You write your message in plaintext. At this point, it’s still unencrypted and could be intercepted if sent as is.
- A unique symmetric session key is generated: PGP generates a random symmetric key (called a session key) using a secure random number generator. This key will be used to encrypt the actual message.
- Your message is encrypted using the session key: A fast encryption algorithm, like Advanced Encryption Standard (AES), is used. This makes encryption and decryption efficient.
- The session key itself is encrypted with the recipient’s public key: Only the recipient’s private key can decrypt this session key. This added layer of protection makes it so that both your email and the key to decrypt the email are inaccessible.
- The message is signed (optional but common): A cryptographic hash of the plaintext message, such as Secure Hash Algorithm 256 (SHA-256), is created, then encrypted with your private key to generate a digital signature. The recipient can verify this signature using your public key to confirm authenticity and message integrity.
- The message is sent: The final message includes:
- The encrypted message
- The encrypted session key
- (Optional) The digital signature
This hybrid system ensures speed (via symmetric encryption) and secure key exchange and verification (via asymmetric encryption).
- The recipient verifies authenticity, then decrypts: Upon receiving the message, the recipient uses your public key to verify the signature (if present). Then, they use their private key to decrypt the symmetric session key. Finally, that session key is used to decrypt the actual message content.
Is PGP encryption secure?
PGP is one of the safest ways to secure your sensitive files and messages. It uses powerful encryption algorithms and a public-key system designed to keep your content private. However, it does have some notable limitations. Let’s take a closer look at both its pros and cons.
Advantages of PGP
PGP’s biggest advantage is that you control your encryption keys. You don’t need to rely on a third-party source to safely store and manage them for you. This means only someone with your private key can decrypt your messages, no matter who tries to intercept them.
PGP also lets you digitally sign emails and files. Adding a signature proves the content really came from you and was never altered during transit by a bad actor.
Another advantage is versatility: PGP is an interoperable protocol that is used in a variety of tools, including secure email providers and command-line software like GNU Privacy Guard (GPG). This means that you’re not locked down to one PGP provider; you’re free to choose whoever you want.
Limitations and metadata exposure
While PGP is excellent for keeping the contents of your message or file secure, it has some limitations. Specifically, it does not hide the metadata of messaging, including email headers, subject lines, and the fact that you’re communicating.
This means that if someone is actively watching your network traffic, they can still see who you’re contacting and when, even if they can’t read your message.
Another problem is that PGP also puts the burden on you to protect your private key and remember your password. If your device becomes infected with malware, you become a victim of a phishing scam, or if you lose your password, your encrypted data could become permanently inaccessible.
Overall, PGP has a wide variety of security benefits, but it doesn’t encrypt the metadata from your messages, and if you lose control of your private key, you may lose access to your files.
PGP vs. GPG vs. OpenPGP
PGP is software created by Phil Zimmermann in the early 1990s. OpenPGP is the official standard (currently RFC 9580) based on that technology. OpenPGP is what is used in a wide range of security tools.
GPG is the most popular open-source software made with the OpenPGP standard. When you generate a PGP key today, it’s typically through GPG.
Functionally, they all provide strong encryption and digital signatures. The differences are mainly historical or relate to licensing and specific features. If you need to secure your email, any PGP protocol from a reputable source will help.
How to set up PGP on your device
Setting up PGP is simpler than it used to be. Today, you can use secure email providers with built-in PGP or install software that integrates directly into your existing email client. The key is to pick the right tool for your needs and platform.
Install and set up your PGP software
Installing your chosen PGP tool is straightforward and usually only takes a few minutes.
First, determine what type of PGP software you want to use. In general, you have two choices: a dedicated email service with built-in PGP protection like ProtonMail or Gpg4win, or a plugin like Mailvelope to encrypt emails for popular platforms like Gmail.
The plugins are a convenient way to encrypt emails from existing email accounts, but you should use a standalone option if you’re seeking a dedicated secure email account.
Here’s how you can get it set up in a few minutes.
- Choose a PGP-compatible app or plugin.
- Download and install the software following the official instructions.
- Open the app or extension and look for the encryption or OpenPGP setup menu to begin setting it up.
Create your PGP key pair
Your key pair is the root of what makes PGP secure. Here’s how to generate the public and private keys needed to make it work.
- Fire up your PGP software to generate a new key pair.
- Enter your name and email address as requested.
- Create a strong, unique password to protect your private key. It’s best that you generate and store strong passwords using a password manager like ExpressKeys.
- The tool will then generate a linked public and private key on your device.
Save your recovery or backup information
If you lose your private key or passphrase, you lose access to your encrypted data. Because of that, make sure you begin by saving your recovery and backup info.
- Export your private key to a secure, encrypted backup file or location.
- Write down your passphrase and store it safely offline.
- If the software offers recovery phrases or printable backups, keep these in a secure place, such as ExpressKeys’s vault. Losing this passphrase means losing access to your PGP tool.
Share your public key
To let others send you encrypted messages, you need to give them your public key. This part is simple and doesn’t expose your private information.
- Export or copy your public key from your software.
- Send it to the contact that you need to send or receive encrypted content from.
- If you use PGP for journalism or other important work, consider uploading it to a key server or adding it to your email signature so others can easily find you.
Encrypt and sign messages or files
Once your setup is complete, you can start encrypting emails and files.
- Compose your email or prepare your file as usual. While in this plaintext format, it is not yet encrypted.
- Click your software’s Encrypt and Sign options. Many services will automatically sign it for you. If it doesn’t automatically sign your email, you will need to turn that option on from within your PGP software.
- Select your recipient’s public key from your keyring.
- Send the encrypted message or file as normal.
Decrypt and verify incoming messages
Decrypting is just as easy as encrypting. Your software handles most of the work.
- Open the encrypted message or file in your PGP software.
- Enter your passphrase when prompted to unlock your private key.
- The software will automatically decrypt the content and verify the sender’s signature, so you can be sure it hasn’t been tampered with.
Update or revoke your keys (if needed)
If you think your keys have been compromised, you should invalidate and replace them. Here’s how.
- If your private key is ever lost or compromised, generate a new key pair right away.
- Publish the new public key and tell your contacts to stop using the old one.
- Optionally, some tools let you issue a revocation certificate, which flags your old key as invalid on public key servers.
PGP encryption use cases
You should use PGP encryption whenever you want to keep important communications or files protected. Here are a few examples of PGP use in the real world:
- Journalists and whistleblowers: PGP helps secure emails and documents so only the intended recipient can read them. It’s often used to share sensitive materials during investigations.
- Businesses and enterprises: Companies use PGP to encrypt internal and external communications, protecting trade secrets, contracts, and customer data. Digital signatures also help verify senders and prevent phishing attacks. In many industries, using PGP supports compliance with privacy and data protection laws.
- Personal communication: Privacy-oriented users can employ PGP to keep private emails and files secure from prying eyes, including internet service providers or email platforms. Encrypting messages with someone’s public key ensures only they can read them, and signing communications proves they came from you.
FAQ: Common questions about PGP
How do I get a PGP key?
To get a Pretty Good Privacy (PGP) key, all you need to do is install PGP-compatible software on your device. Most modern PGP software will handle the complex parts, such as generating and sharing your encryption keys with recipients.
Is PGP the same as GPG or OpenPGP?
PGP, GPG, and OpenPGP are closely related but have some differences. PGP stands for Pretty Good Privacy. It was a software security protocol that was developed in the early 90s.
OpenPGP is the standardized protocol that came from PGP’s design. It’s publicly available and has been adopted by a wide range of security services, in addition to receiving several updates over the years.
GPG, or GNU Privacy Guard, is a widely used open-source version of OpenPGP. It allows a user to set up a PGP on alternative operating systems, like Linux. If you create a PGP key today, it’s most likely being created through OpenPGP-compatible software.
Can PGP be cracked?
Theoretically, any encryption service could be broken, but Pretty Good Privacy (PGP) remains highly secure when modern, strong algorithms and properly managed keys are used.
PGP offers users the choice between multiple encryption algorithms, including 256-bit Advanced Encryption Standard (AES) and Twofish. It also supports some legacy encryption models, like Carlisle Adams Stafford Tavares (CAST5), the old default encryption solution. Not all of the supported encryption algorithms are equally secure, and users should avoid legacy options.
Another issue is that PGP lacks perfect forward secrecy, which means that, if your private key is compromised, all emails encrypted with that public key become decryptable.
New threats are also emerging, such as store-now-decrypt-later attacks. During these attacks, someone collects your encrypted information while waiting for decryption breakthroughs in quantum computing.
Does PGP hide metadata?
No, it encrypts the contents of a specific message or file, but it does not hide metadata. This means it offers no protection for email subject lines, sender and recipient addresses, or the time you sent the email.
If you use Pretty Good Privacy (PGP) with email, your email headers remain visible to anyone observing your traffic. To optimize your privacy using PGP, try using generic subject headers. A VPN will also encrypt your traffic in transit, meaning you could use ExpressVPN and OpenPGP to protect your metadata from being spied on by third parties, though the email provider will still see it.
Is PGP still used?
Yes, Pretty Good Privacy (PGP) is still widely used today, through OpenPGP and the range of services that use it. A wide range of privacy-focused email services, file encryption tools, and software update systems still use OpenPGP to encrypt sensitive files and emails.
Even though communication is largely handled by secure messaging apps nowadays, PGP is commonly used in services that require a deeper layer of protection.
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN