What is a browser-in-the-browser (BitB) attack?

In a browser-in-the-browser (BitB) attack, a hacker creates a fake login window that looks completely real. It includes all the visual cues you expect to see, such as a browser frame, a padlock icon, and a legitimate-looking web address. But none of it is genuine.
These attacks are especially effective because they imitate single sign-on (SSO) prompts from platforms like Google and Microsoft. Most people are used to seeing these pop-ups and don't question them. The experience feels normal, even when it's entirely fake.
This article explains how BitB attacks work, why they’re hard to detect, and how you can avoid falling for one.
Understanding browser-in-the-browser attacks
What makes BitB attacks unique among phishing techniques?
Most phishing attacks follow a familiar pattern: you click a link and get redirected to a fake website, something like fake-bank-login.example.com. If you're paying attention, you might notice the suspicious URL or strange design before entering your credentials.
BitB attacks take a different route. When you visit a website controlled by the attacker, you’re presented with what looks like a legitimate SSO window directly within the current page. No new tab, no change in the address bar, and nothing that breaks the illusion.
Because the window looks familiar, many users won’t question it. They’ll simply opt to “Sign in with Google” or “Log in with Microsoft” and enter their credentials as they usually would.
But the window isn’t legitimate: it’s built using front-end code (think HTML, CSS, and JavaScript) to copy what a real browser login pop-up looks like. Even the padlock icon and URL bar are faked. And when the credentials are entered, they go straight to the attacker.
Why do cybercriminals use phishing messages to initiate BitB attacks?
BitB attacks need bait. Attackers have to get you onto their rigged webpage somehow, so they'll use whatever works. It could be a phishing email claiming you need to review an "urgent document" or maybe a fake shopping site advertising a too-good-to-be-true discount.
Once you land on their page, that's when the trap springs. The site immediately shows you a login window that looks exactly like the real Google or Microsoft sign-in page. This combination of psychological pressure and visual trickery has made BitB a go-to method for scammers in recent years.
How does a browser-in-the-browser attack work?
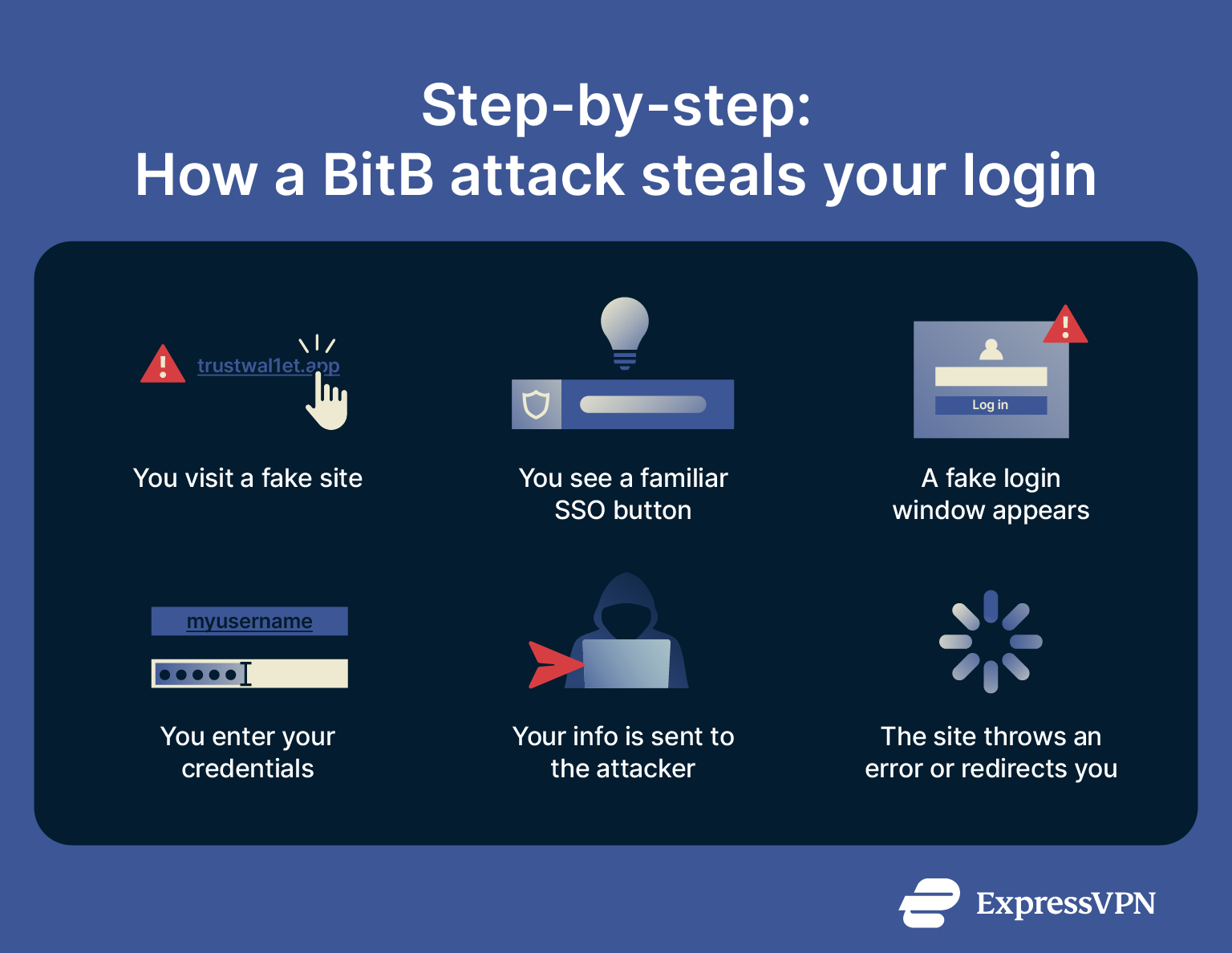 BitB attacks follow a fairly predictable pattern. Here’s how it usually plays out:
BitB attacks follow a fairly predictable pattern. Here’s how it usually plays out:
- You land on a fake site: Maybe it came from a phishing email or a link that looked legitimate. Either way, the page looks convincing, sometimes even identical to a real site.
- You see the usual SSO options: There's a “Sign in with Google,” “Log in with Microsoft,” or similar SSO button. It looks exactly like the real thing.
- A “login window” pops up: It looks like a browser pop-up, but it’s not. The site builds it using HTML, CSS, and JavaScript to mimic every detail. Even the URL inside the fake address bar can be spoofed to show something like https://accounts.google.com, making the window appear completely legitimate.
- You enter your credentials: Everything looks normal, so you type in your email and password like you always do. But the entire window is fake, and everything you enter goes straight to the attacker.
- The attacker might even grab your two-factor authentication (2FA) code: Some BitB attacks prompt for 2FA and hijack your session in real time.
- The site covers its tracks: After you submit, it might send you to the real login page or throw an error like “Incorrect password.” You think you just mistyped, but by then your info is already stolen.
The role of SSO in BitB attacks
BitB phishing works because it exploits learned behavior. You expect a login window from a different domain (like accounts.google.com) to pop up when using SSO, and the fake login matches what you already trust: a separate window, the right domain, and a padlock icon. BitB replicates the SSO flow perfectly.
What makes this worse is that SSO credentials don’t just unlock one account. A single Google or Microsoft login can grant access to emails, cloud storage, internal apps, and more. One successful phish can compromise several accounts.
Visual mimicry and iframe deception techniques
- Recreating the browser window: Using nothing but HTML and CSS, attackers can fake an entire browser window. They'll recreate the title bar, window borders, close buttons, and a fake address bar complete with the right font, favicon, padlock icon, and https domain. Add some dropshadows and overlays, and the illusion is complete.
- Cloning the login form: The fake window uses an iframe or a copied version of the real login form. Since Google and other providers block iframe embedding, attackers usually go with static HTML that looks identical to the original. They copy everything: the logos, input fields, and even the "Forgot password" links.
- Spoofing hover behavior: Some users are smart enough to hover over links before clicking to check where they lead. Attackers know this, so they'll make the login button show a legitimate URL when you hover over it, then use JavaScript to hijack your actual click and open their fake window instead. You think you're being careful, but you still fall into the trap.
Behind the scenes, any credentials you enter are silently captured. Attackers often use a method called AJAX, which lets the site send that data in the background without refreshing the page.
Real-world examples of browser-in-the-browser attacks
When the BitB technique was first publicized by security researcher mr.d0x in early 2022, it was largely a proof of concept that security professionals warned about. For a while, BitB was theoretical; many wondered if real attackers would bother using it. But now it’s showing up in real-world phishing campaigns across both consumer and enterprise targets.
Notable proof-of-concept demonstrations
The original demo by mr.d0x revealed how easily a web page could be made to impersonate a browser window. His fake Google login pop-up didn’t just resemble the real interface: it recreated it in precise detail. The purpose was to show that even tech-savvy users could be fooled if they relied solely on visual cues like the URL.
mr.d0x released templates for these fake windows, with versions tailored for Chrome on Windows and macOS in light and dark modes. Even low-skill attackers could now deploy convincing BitB attacks that were nearly indistinguishable from the real thing.
The security community quickly picked this up. Researchers expanded the demo with cloned login flows for Microsoft OAuth and other SSO providers and subtle design details like transparent overlays, correct favicons, and timed popups triggered by login buttons.
It didn’t take long for cybercriminals to follow suit. Open-source BitB templates started appearing in the wild. By 2023, researchers observed phishing emails that embedded BitB-style pages inside HTML attachments.
If the user opened the file in a browser, it would instantly display a fake Office 365 login pop-up, skipping past common email filters.
BitB in real phishing campaigns
- Steam gaming campaign (2025): Attackers created fake tournament and eSports websites to lure gamers. When users tried to log in, a BitB-style Steam login window appeared. The goal was to steal credentials from accounts that held valuable in-game items, which could be resold for real money.
- Cloudflare pages campaign (2024): A similar operation used Cloudflare’s pages.dev platform to host phishing sites. The trusted-looking domain helped avoid suspicion, and the same BitB technique was used to spoof Steam’s login flow. It highlighted how infrastructure abuse can add credibility to the attack.
- Belarus-linked Ghostwriter campaign (2022): The Ghostwriter group, a Belarusian threat actor, used BitB to simulate a login page for passport.i.ua, a popular Ukrainian email provider. The fake pop-up appeared over a compromised website, tricking users into entering credentials. Once submitted, the stolen credentials were sent to a domain controlled by the attackers.
How to detect and avoid BitB attacks
How to spot a fake sign-in prompt
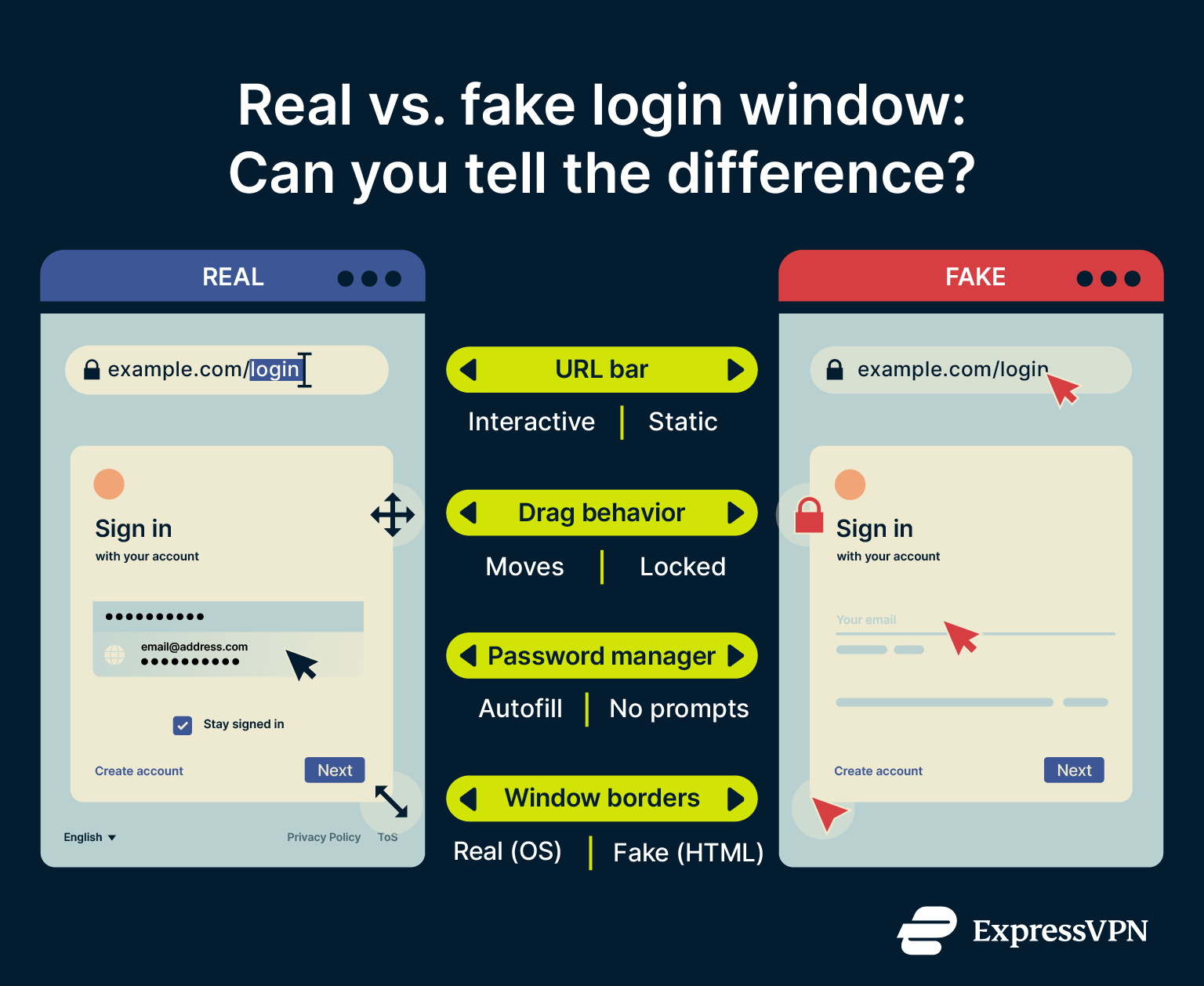 BitB attacks are designed to look real, but they don’t behave entirely like real windows. Here’s how to spot one:
BitB attacks are designed to look real, but they don’t behave entirely like real windows. Here’s how to spot one:
- Try to move the window inside and outside the browser: Real browser pop-ups are separate operating system windows. You can drag them freely across your screen, even outside your browser. BitB windows often allow limited dragging to appear realistic, but they’re still stuck inside the webpage. If you try to move the window beyond the browser frame, it may snap back or stop entirely. That’s a clear sign it isn’t real.
- Inspect the address bar carefully: Don’t just glance at the URL displayed in the pop-up. Try clicking or selecting it. On a real login page, the address bar is functional: you can copy the URL, see it change if you navigate away, or right-click to get standard browser options like “Back” or “Reload.” In a BitB attack, you might be able to highlight the address bar, but nothing else. Right-clicking may bring up a basic web context menu or nothing at all.
- Watch for visual inconsistencies: BitB windows can look highly convincing, but small details may still give them away. Check whether the theme matches your system (dark or light mode), if the language feels off, or if the fonts and icons look even slightly unusual. Minor mismatches can be a sign that the window isn’t real.
- Ask yourself if the login makes sense right now: Were you expecting to authenticate? Random login prompts on unfamiliar sites are a red flag, especially just after clicking a link. Always pause and verify.
- Check how it looks on mobile: BitB attacks rarely work well on phones. If a floating pop-up appears instead of a full-page login, it’s probably fake. Legit mobile authentication rarely uses separate window-style prompts.
- Note password manager behavior: If your password manager normally autofills on Google or Microsoft logins, and it’s suddenly not working, that indicates it’s not a legitimate login window.
Security tips for end users
Even the sharpest users can be fooled by a polished BitB window, so it’s important to maximize your protection against them:
Use two-factor authentication (2FA)
Enable 2FA on every major account. It won’t stop the phishing attempt, but it can block account access even if your credentials are stolen by requiring another proof of identification.
Keep your system updated
Always install browser and OS updates. While BitB isn’t a traditional exploit, updates help browsers block malicious scripts, which can make it harder for fake login windows and other threats to slip through.
Use a password manager
Password managers only autofill credentials on secure, recognized domains, making them an effective tool to avoid entering details into fake login windows. ExpressKeys also offers zero-knowledge encryption, breach alerts, and built-in 2FA support.
Be selective with SSO
Don’t use “Sign in with Google” or “Login with Facebook” on every site. If you don’t know or trust the platform, skip the SSO entirely. And if you do use it, verify by opening the provider’s login page in a separate tab.
Check the login behavior, not just the look
BitB traps can mimic real SSO windows, but they can’t fake browser behavior perfectly. If you can’t click the address bar, move the window freely, or open it in a separate tab, it’s likely fake. When in doubt, close the tab and access the login page by typing the URL yourself.
Use smart tools to catch phishing attempts
Some browsers and security extensions can help detect BitB-style attacks by isolating popups, blocking shady scripts, or flagging phishing domains. ExpressVPN’s Threat Manager blocks access to known malicious sites and trackers before they load, giving you an extra layer of defense when browser warnings fail.
Ways to protect your organization from BitB attacks
BitB phishing can target organizations as well as individual users. With the right tools and policies in place, companies can mitigate these attacks.
Use multi-factor authentication (MFA)
Even if credentials are stolen, MFA prevents access without a second factor. To be effective against BitB, use phishing-resistant MFA methods, like hardware keys or app-based prompts that verify the site’s domain.
Enforce MFA across all user accounts, especially email, VPN, and SSO. VPNs are a common target, as they often grant access to internal systems. For admin and high-privilege users, add stricter login controls; a stolen password should never lead to full access.
Ensure web browsing is secure
Stop users from ever reaching phishing pages by using Domain Name System (DNS) filtering and secure web gateways, which can block access to malicious or suspicious domains that host BitB kits.
To go further, use browser isolation for untrusted links. Opening risky pages in a sandbox prevents scripts from stealing data, even if the user is fooled.
Keep browsers updated and limit pop-ups to whitelisted domains to reduce exposure. The fewer login prompts users see, the more suspicious they’ll be of unexpected ones.
Use endpoint protection systems (EPS)
Modern endpoint security tools can flag behavior typical of BitB kits, like cloned login forms, suspicious scripts, or credential theft patterns. Some can block these in real time.
BitB attacks sometimes also arrive via HTML email attachments, so configure email gateways to detect and block risky file types.
If possible, deploy managed browser extensions that flag spoofed login elements or alert users when domains don’t match expected authentication flows.
Check user access privileges regularly
Limit what each user can access. That way, if credentials are compromised, the damage is contained. Audit access rights frequently and watch for unusual login activity: new devices, odd times, or rapid failed attempts. Many identity providers (like Okta, Azure AD, or Google Workspace) can alert you when accounts behave abnormally.
Also have an incident response plan ready. That way, if a BitB attempt is reported, you can take action quickly to revoke credentials, notify affected users, and scan for other signs of compromise.
FAQ: Common questions about browser-in-the-browser attacks
What is a browser-in-the-browser attack?
It’s a phishing technique that fakes a browser window inside a webpage. You see what looks like a normal single sign-on (SSO) login popup, but it's designed to steal your credentials.
Why do attackers use fake login windows?
Because they work around your natural suspicions. Most of us have learned to trust the appearance of a secure login box: the padlock, the familiar design, and the right domain name. Browser-in-the-browser (BitB) attacks take advantage of that trust by copying browser behavior and mimicking domains we recognize.
Are BitB attacks common in the wild?
They’re growing. Once just a proof of concept, browser-in-the-browser (BitB) attacks are now used in real phishing campaigns targeting both consumers and businesses. They're less common than basic phishing but far more convincing.
Can antivirus software detect BitB attempts?
Sometimes, but don’t count on it. Browser-in-the-browser (BitB) attacks run in the browser, often using clean scripts on unfamiliar domains. Some advanced security tools can flag suspicious behavior, but detection isn’t guaranteed. Prevention and user awareness matter most.
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN